Confidential Communications Blog
Latest Posts
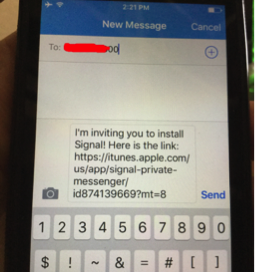
Signal: Using the right tool for the right job
In today´s world where privacy, anonymity and confidentiality are a required in our day-to-day communications, those features are something most users expect when using a communication tool such as Signal from Open Whisperer Systems. Unfortunately a lot of users tend to mix or use as synonyms each one of those concepts when in reality they […]

Lawyers slow to adopt email encryption and other forms of secure communications, ABA survey finds
We re-print here a short article from the ABA Journal of October 5, 2015 which provides some numbers for various concerns we often express to law firms when we find security issues with electronic communications that might negatively impact their clients, in particular whistleblowers and qui tam relators: If you’ve ever received an email from […]
Our choices for more secure and confidential communications
Why are we changing our phone service? We have for several years used a Skype telephone service to receive general voicemails. However, since last fall, we have had continual issues keeping that service functioning. Recently, for example, we learned that calls we made to the service went to voicemail, consistent with our longstanding program preferences. […]
Digital Identity and Metadata
The fight to stay anonymous People by nature want to keep certain aspects of their life private, anonymous; others because their jobs require to stay anonymous and others because what they are doing could lead to repercussions in their professional and personal lives. The funny thing is that most people think that just because they […]

Service Provider Blocks Tor to Silent Circle Claiming Security Threat
Service Provider Blocks Tor to Silent Circle Claiming Security Threat January 21 2015The Claim:”Tor exist nodes are routinely used as methods by Threat Actors to exfiltrate data from compromised endpoints. As an example, the Financial Sector has seen significant issues from them.“ FireHostThe Issues:• Bad guys use it; let’s treat everybody as bad guys • […]
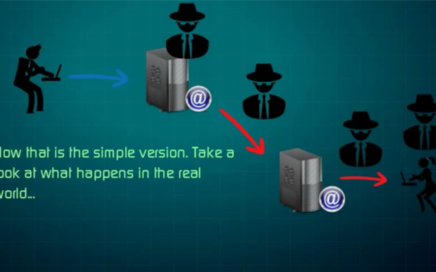
Email insecurity video
This article is a the first in a series aimed to people who are looking to understand the risks of using the internet as a primary communication channel, especially for sensitive subjects. Let’s start with something that has become an indispensable tool for communication in our world and I’m referring to the email. Email can […]






