The fight to stay anonymous
People by nature want to keep certain aspects of their life private, anonymous; others because their jobs require to stay anonymous and others because what they are doing could lead to repercussions in their professional and personal lives. The funny thing is that most people think that just because they are seated in front of a computer, it automatically grants them anonymity, and that is far from the truth. In this article I will try to explain some issues that any person using the Internet should be aware in order to look for mechanisms to help maintain his/her anonymity.
Digital identity
The first issue is our digital identity; this is formed by our usernames, email addresses, and accounts across
the Internet. Given the impressive power of search engines such as Google one should pay more attention of our digital identity and how we use it.
When was the last time you posted/sent/signed in with your email account? All those logins, accounts, etc usually are linked to an email and they become a trail pointing back in your direction and if you add to all this the use of social networks, well, let me tell you that the person behind the keyboard is no longer anonymous as he/she once thought. In fact a skillful adversary with enough resources will be able to identify a user including a nice photo from his last birthday party that was posted on Facebook.
If you are planning to achieve certain degree of anonymity, the first step is to create a second virtual id, one that is going to be used only for those activities that will require anonymity. [Editor’s note: a virtual ID is one form of alias or pseudonym. We will have a separate post on the history of aliases, pen names, handles, and similar concepts.]
It is important not to mix both identities. Sounds simple but human beings are lazy so you need to think like a
super hero, you have two IDs, one that is being used for your everyday activities and the other one that for that activity that requires you to maintain anonymity.
Now having two IDs is not enough to maintain anonymity, but is the first step; in reality to maintain anonymity you will require several technical and procedural measures in order to avoid being tracked or at least make it very difficult for a potential adversary. Some of the measures that you will need to maintain anonymity are:
-
Changing as much as possible your physical location to access the Internet
-
Using software that improve anonymity such as TOR
-
Use of encryption and secure communications channels
-
Become a little bit paranoid.
Also your chances will improve if you understand that there is no 100% guarantee that you will maintain anonymity and in order to decrease the risk of being identified the use of several technologies is recommended. In security this concept of layers of several security mechanisms is known as defense in depth and should be something you must look for.
Metadata
Metadata is defined as “Data that provides information about other data” (Merriam-Webster.com). All our technological wonders that we use in our daily lives have embedded plenty of metadata. A photo taken from your smart phone, a Word file report, the email you send to exchange greetings with friend; all of them have these tiny bits of information that could allow an attacker to track you and pinpoint your identity.
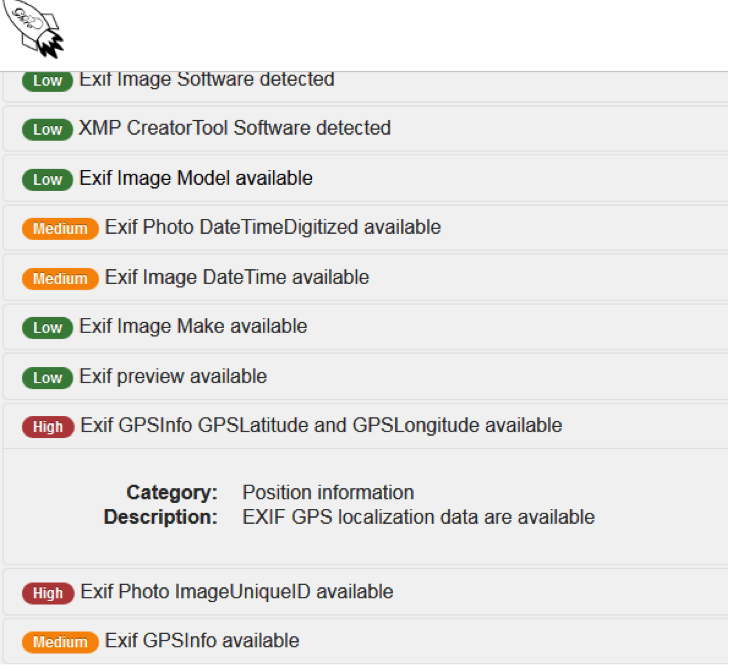
The following is a clear example regarding metadata that will help enlighten you about what kind of information about yourself could be revealed without you being aware. Photos in jpg format like the ones taken with the camera of a smart phone stores its metadata in a standard format known as exif (exchangeable image file format) and can contain the following information:
-
Date and time when the picture was taken
-
GPS data: if the device has this future active it will add this information in the image, with the current trend with social media apps usually this feature is on and most users are not aware or don’t mind
-
Make and model of the device: An attacker could use this info to prepare a more specific attack and try to gain access of your device either remotely or physically
-
Serial number of the device: Allows identifying a particular camera or Smartphone
-
Image Unique ID string for each picture: The string allows a resourceful investigator to link the photo to a specific camera or Smartphone
Some tools that you could use to check the exif information in an image are http://www.imageforensic.org/ and Jeffrey’s Exif Viewer at http://regex.info/exif.cgi both offer a very simple interface and will let you see what kind of information that images has about you, your location or device that was used to take the picture. The following picture shows what imageforensic.org online tool will reveal:
Now, the example shows what metadata is embedded in a photograph taken with a Smartphone, but that is not the only source of metadata. Almost all applications running in a computer or the Internet creates metadata and add it to our files. For example:
-
Office applications can embed metadata in any document about the author that could reveal his identity, when was created, if it was modified and in some cases the changes the document have
-
Image manipulation software also could include metadata with our location (i.e. Photoshop)
-
Most email clients include metadata in all the emails we send that could include our IP address, computer information and in some cases the real identity of the user.
So in order to maintain anonymity a user must sanitize the information he/she plans to share to avoid giving up information that could be harmful in the future. There are several tools available in the Internet that will help in removing personal or identifiable information from a file. Keep in mind that most tools specialize in only one type of file (images, Office, Documents, PDF files, etc) so it’s impossible in a brief space to discuss all of them. In the case of images tools such as Batch Purifier LTE (http://www.digitalconfidence.com/downloads.html) and JPEG and PNG Stripper (http://www.steelbytes.com/?mid=30) are free and very easy to use in order to remove metadata from images.
Web Beacons/Web Bugs
Web Beacon is a method that goes by several different name such as “web bug”, “pixel tag”, “clear GIF”, “invisible GIF” originally designed to pass information from the user’s computer to a third party web site while the user navigates thru a web page. Now this kind of technology allows several other uses, such as tracking when a user has opened a document or an email. Usually a web bug is a one pixel transparent image object (GIF is the most common format) that is defined by HTML code and that code to a specific site. In order to see web bugs and other tracking methods in action the user can install a plug-in called Ghostery (https://www.ghostery.com/en/download) available for most browsers. Once configured you will receive a small pop-up that indicates who is trying to track you, and it’s amazing the number of trackers some web sites have.
The following screen shoot shows Ghostery in action:

In the screen shot we can observe Ghostery is displaying the websites trying to track you the moment you visit www.amazon.com. Ghostery has the option to block the websites trying to use any of the following devices for tracking:
-
Analytics Object
-
<Beacons
-
Cookies
-
Widgets
-
Advertising objects
Ghostery has a database that is constantly updated improving the blocking of the tracking objects that a web page might contain, but is not 100% effective. Unfortunately Web beacons and related technologies such as cookies, scripting languages, etc. makes it very difficult to maintain your anonymity.
A good defense against Web beacons and similar technologies is the use of several mechanisms (remember defense in depth?), such as TOR (https://www.torproject.org/), use of specialized environments optimized for secure operations like Tails (https://tails.boum.org/), secure communications and encryption (https://www.gnupg.org/), opening attachments or documents in an isolated machine not connected to any network (“air gap”) and finally taking into consideration the points discussed about your digital identity and metadata.
I hope this article serve to open your eyes and become aware of what is required to attain true anonymity so, the next time you login, open, send, or browse something in the internet ask yourself this: “What information about myself I’m revealing without knowing?”
